After starting your personal computer the application you intuitively reach for with your mouse pointer is the web browser. Most web browsers greet you with a input field of all input fields - the search box. Once you do a search you eventually arrive at a website.
While evaluating and working on your own website and content management system. You have most likely arbitrarily pieced together the architecture of your website. Resulting of Your website being served by the ubiquitous application shell - web browser. Web browser residing on your website's end user's device sending a request to your website's domain name. The domain name pointing to a server hosting your website.
The web browser, making a request to web server, for the document being requested, and the data transaction passing through the various separation of concerns. Server side script engine, web server, http packets, transmission control protocol, wide area network, local area network, and arriving at a users web browser.
Some if not most prefer the web browser to interpret and display the responses from a web server as a desktop application. This misunderstanding has resulted in over burdening and abusing a simple client side scripting language - JavaScript.
There are separation of concerns within the web browser it self. Most recently introduced separation is sand-boxing of displayed content in browser tabs.
Beside the browser tab. HTML markup organizing web content for display, CSS style sheet for stylizing web content, and JavaScript best suitable for sprinkling interactivity.
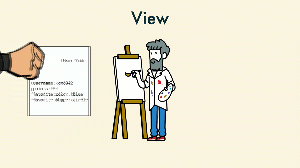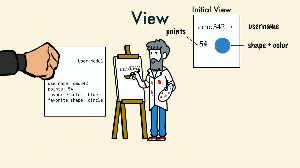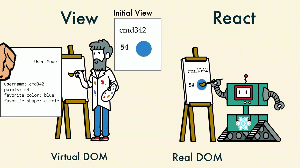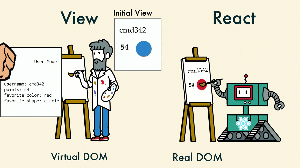
The excessive preference and exaggeration of a scripting language has resulted in the most advance computer science rigging feats. To the extent the web browser has a virtual machine called a JavaScript engine. Even beyond this the virtual machine is now required to host additional information resulting from a simple request and allow the subsequent responses to manipulate this information inside the virtual machine - virtual document object model.
The imbalance of exaggerating a simple scripting language results in further imbalance. CSS styling is also relying on the scripting language engine to store variables and animate html objects. This was supposedly the job of JavaScript. Many countless security concerns have been the by-product of this imbalance alone.
The various types of developers who would otherwise be repairing and improving content quality. Instead are being herded from one JavaScript framework tool chain to another.
The original intent of the web browser was simply to display properly formatted text and animated Gifs for the scientific community. For the intended purpose the browser wasn't a security threat to the user. Since then as the Internet progressed along with the web browser, with introduction of JavaScript, plugins, and most recent memory management rigging inside the browser, virtualization of the document object model, threats began to appear. The virtualization of the DOM breaks the separation of concern by creating a client server architecture within the web browser's memory. This breaks the existing external client server model as well and introduces security issues.
Further reading
"Nov 9, 2016 - Google is tackling high memory consumption by its Chrome browser, ... problems as Google highlighted in a study of 760,000 sites caught by Safe Browsing." (https://www.zdnet.com/article/google-to-malware-sites-well-brand-you-deceptive-for-a-month-no-reviews-allowed/)
"760,000 sites..""Feb 22, 2016 - The website has been down for most of Sunday, potentially losing thousands of downloads. ... Chrome: 70% of all security bugs are memory safety issues." (https://www.zdnet.com/article/hacker-hundreds-were-tricked-into-installing-linux-mint-backdoor/)
"..memory safety issues.""Mar 11, 2020 - Academics break TRR protections on RAM cards for new Rowhammer attacks. ... The list below summarizes the most important papers and advances in Rowhammer attacks: Academics showed how a.." (https://www.zdnet.com/article/modern-ram-used-for-laptops-smartphones-still-vulnerable-to-rowhammer-attacks/)
"Academics break TRR protection..""May 23, 2020 - Chrome: 70% of all security bugs are memory safety issues ... These memory management vulnerabilities are the most sought-after bugs that ... and have recently rolled out Site Isolation, a feature that puts each site's resources into its ... cyber attacks.." (https://www.zdnet.com/google-amp/article/chrome-70-of-all-security-bugs-are-memory-safety-issues/)
"..70% of all security bugs.."